But all of those cases apply equally whether using Windows 10, or Windows XP, which is what we are talking about.
What is less secure?
And if you are only using Dropbox to store some non-confidential or public domain PDFs anyway, who cares?
People get all hung up on obscure vulnerability XYZ while ignoring more important basic security measures.
Weak passwords will always get you, but having an exposed password prompt is never a good idea anyway. We run a server at work and have hacking attacks running H24, a new password tested every few seconds. The server is as secure as can be but you would not want to run Windows (any version) exposed like that, due to all the various malformed packet attack vectors.
The other thing which will always get you is I believe called social engineering. Somebody posts a pic whose EXIF shows he has a particular type Sony camera. So you email him an email entitled “Latest firmware for your camera type XXX” and going to a dodgy website of with a dodgy attachment  Most phone pics also show other stuff e.g. location, and often the full name of the person who took the pic.
Most phone pics also show other stuff e.g. location, and often the full name of the person who took the pic.
A friend of mine used to work at Cisco and he got one of his security guys to hack peter2000.co.uk (with my agreement). The guy could not find anything, despite the site running on my home ADSL back then, but he pointed out the Sony camera route as usually working quite well 
You do need to be running AV software because a lot of PHP-BB forums (not EuroGA) get infected. Almost all of the UK sites have got it at some stage.
As for the Dropbox topic I still have not seen a good reason to block a particular OS for which a client currently exists.
We had an IT manager who didn’t believe in updating operating software if it was working.
That was great while it lasted.
Shortly after he left chickens came home to roost big time as software incompatibilities between new and old PCs, new production equipment, customer’s document transfer systems, a new ERP system, and our outdated systems caused serious and expensive problems starting with an update to the virtual server software. That led to the 2000 or so updates to Outlook server that needed to be done before we could update to the next version of Outlook server, then the next, then the next, etc. And email was the tip of the iceberg.
Running old obsolete software is a dead end that in our experience ends badly and needs sorting out eventually. Burying your head in the sand against progress is rarely the best policy.
Somewhat remotely related. I have used a Chromebook a couple of years. Considering the limitations compared with a “full” PC is OK with you, I couldn’t be happier. Especially when travelling, it is very practical. I also got an ancient HP mini that until a few minutes ago run Win 7, and was unusable, too slow to show any web pages, took for ages to boot and so on. These things were called “netbooks” but never really made it. They started off with the Asus EEE, using a light weight Linux OS, but people rather wanted Windows on them, which destroyed the whole concept. (Chromebooks came later and restored that concept, mainly because the concept is executed the way it should be executed).
Chrome OS is a closed OS, and only runs on dedicated Chromebooks. But now (since last October actually), Chromium OS became available for any PC. The OS is distributed by Neverware and is named CloudReady. It is a full fledged Chromium OS with all the goodies from Google, and is of course specially made for “the Cloud”. Installed it a couple of minutes ago, and is writing this on it  And of course it is free, costs nothing for private individuals. It (CloudReady) is however specially made for schools and businesses, with the main point of being super easy to admin.
And of course it is free, costs nothing for private individuals. It (CloudReady) is however specially made for schools and businesses, with the main point of being super easy to admin.
On topic; dropbox will never become outdated on devices running Chromium, and the full space of the hard drive is also available. Then again who needs dropbox? I use Google drive, onedrive, and a few others. It seems like everybody are offering drives in the clouds these days.
Before for more security silliness is spread and folks proposing to switch to Mac or Ubuntu:
Top 50 Trophy Holders 2015:

All time Trophy Holders:
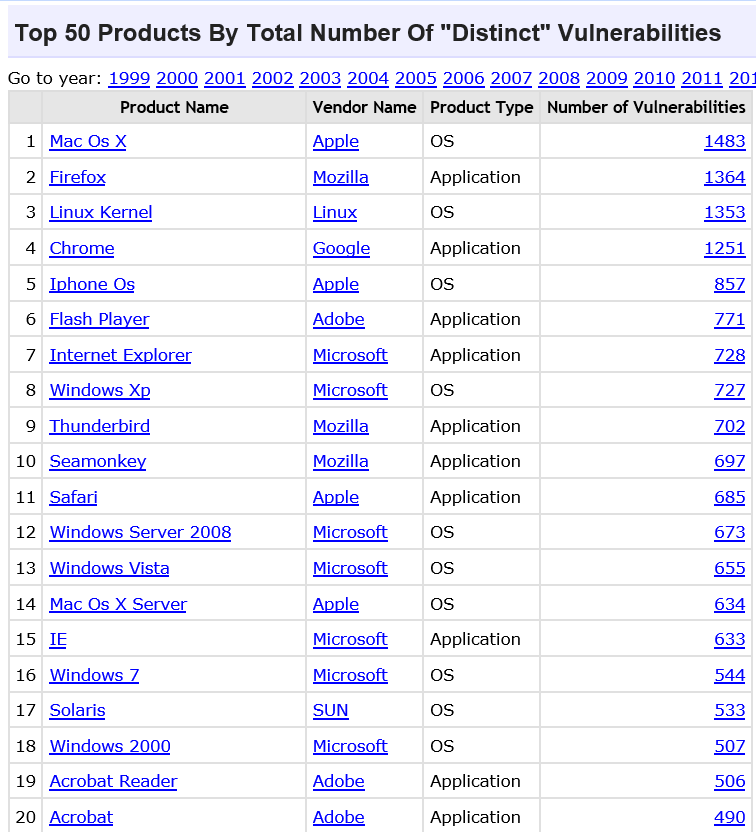
According to secunia security report March 2016:

Source: http://www.cvedetails.com/
For private individuals (i.e., unlikely to be subject to a specific espionage or sabotage effort) this does matter less, because the likelihood of a successful attack is driven not only by the nimber of vulnerabilities, but also by the number of attackers trying to exploit it…
Are there any stats on that? (Just curious)
Lucius wrote:
Before for more security silliness is spread and folks proposing to switch to Mac or Ubuntu:
@Lucius, you conveniently left out the vendor chart, which shows Microsoft securing the top spot far ahead of the competition.
Furthermore, these top 50 charts might be amusing, but they’re completely unusable to assess one’s risk exposure, because they compare apples to penguins.
These charts mix products with vastly different feature sets and compare vulnerabilities of vastly different criticalities.
If we compare Ubuntu Linux to Windows 7, then you can see that of the 544 CVE’s for Windows 7, 165 are in the highest criticality bin, while for Ubuntu, only 32 of the 384 are of the highest criticality variety.
If we look at the highest criticality CVE’s reported this year, we find 3 for Ubuntu. Two affect LibreOffice, but Windows 7 does not even ship with a word processor. The third affects PostgresSQL’s PL/Java binding, but again Windows 7 neither ships a database server nor Java. Furthermore, only very special server applications would likely run PL/Java.
Contrast this to Windows 7: Of the 9 critical CVE’s (8 of them also affect Windows 10), pretty much all of them are exploitable while browsing the web.
This is from the same datasource you used. If you dig down a bit, the picture looks like the opposite of what you’re trying to make it look…
tomjnx wrote:
Microsoft securing the top spot
That’s because Microsoft has by far the largest software portfolio of any vendor. You have to compare software in the same category (OS, Spreadsheets, browsers). Ubuntu is not really a choice for ordinary users (>99%). It’s a tech geek toy, albeit a nice one perhaps, hence not interesting to hackers. One can say, security by lack of popularity.
The comparison that really matters are Apple’s OS (Mac, and iOS) versus Windows. And no matter what data you look at the difference in terms of security are dramatic.
The biggest factor in determining what gets hacked is who is the most hated.
In terms of OS and apps, for many years it has been Microsoft. Bill Gates is just not a popular character, for whatever collection of reasons. It was not Apple because they were riding a big wagon of goodwill as the American Underdog – an image skillfully cultivated by Steve Jobs who by all accounts was not the nicest individual around himself.
In terms of targets, specific websites have been targeted due to controversy, grudges, or just plain ease of doing it. I can think of some well known websites which get hit all the time because they drive controversy. On the last one, it’s apparently been possible to construct a google search which digs out all the PHP-BB based forums and then it’s trivial to test each one whether it has back doors, and if it has you hit it… it’s pure fun for a teenage boy without a girlfriend. A bit like you can search for all the AXIS webcams with an HTTP server, many of which are installed in peoples’ homes 
I still don’t see the issue with dropbox. Apart from hacking the login/password (which gives you access to all of somebody’s dropbox, and the way to get that is the same method(s) you would use to hack anything else protected by a straight login) the only vulnerability I’ve heard of is the one caused by them hashing each uploaded file and if they find the same file already exists on their server, the upload is faked i.e. it happens very fast. So if you suspected e.g. an employee of yours has stored an internal company document, 100MB in size, on dropbox, you could check that by uploading the file yourself and if it uploads in 2 seconds, it tells you that somebody has already uploaded it  And I imagine many people already do this with confidential documents, as a quick and dirty check to see if they have been leaked by somebody clumsy who doesn’t read The Register etc.
And I imagine many people already do this with confidential documents, as a quick and dirty check to see if they have been leaked by somebody clumsy who doesn’t read The Register etc.
All the other stuff is either generic (valid in a broad context but not relevant to dropbox) or applicable to fifty other things or (like whether somebody can wiretap your phone line and get the stuff in clear) irrelevant to normal people. If you are married and shag around and have a computer to which your other half has access, possibly a Mac, then you need to be careful with how your i-message stuff is configured, for example 
If you allow physical access to your machine to uncontrolled persons, you can totally forget security in every sense. And if you allow children physical access to your machine, you will need to reformat the HD a few weeks later 
I think this is the only pilot forum where you would find a thread that turns into a Gates vs Jobs debate!
Bottom line, the whole subject of IT security is too complicated for the average person to understand it or to appropriately manage their risk level. Even IT and software professionals are liable to overlook security issues with the way they use their software tools. Finance is another area where the complexity had exceeded ability of the average person to understand it, even for “simple” products like mortgages or credit cards.
Combined with this there is the strange paradox that people seem obsessed with online security and privacy and yet they don’t hesitate, for example, to post photos of their kids on social media, or continually “check in” and declare their location to the world.